Impressive Tips About How To Protect Public Keys From Tampering

Modification of a user's authorized_keys file by an attacker is prevented by.
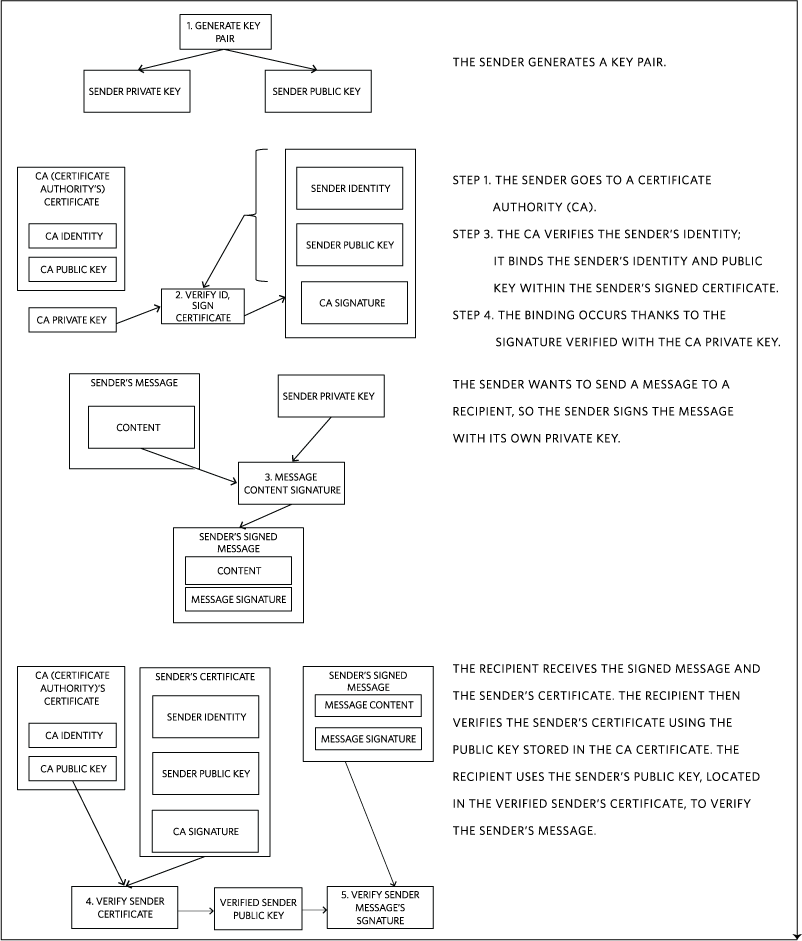
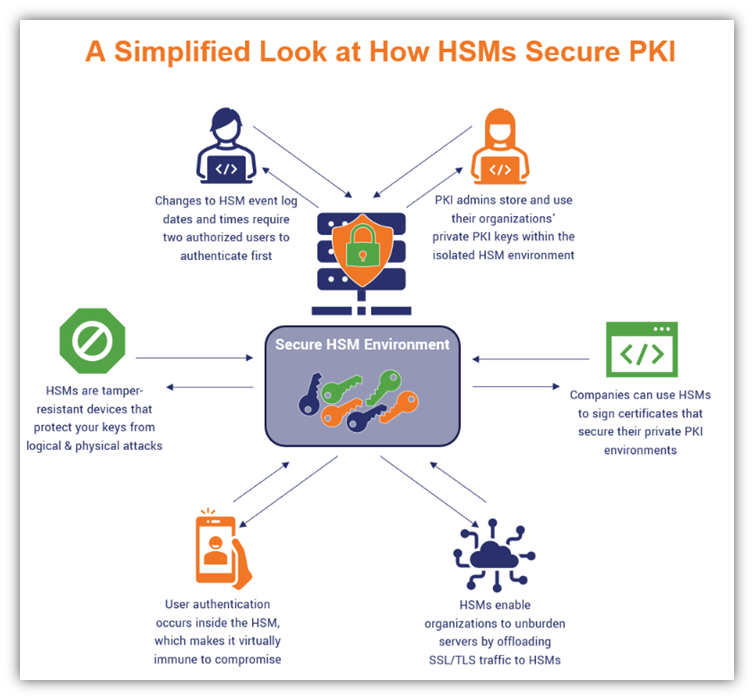
How to protect public keys from tampering. One somewhat complicated way to protect your own whole public keyring from tampering is to sign the whole ring with your own private key. One somewhat complicated way to protect your own whole public key ring from tampering is to sign the whole ring with your own secret key. If a server is compromised, an attacker could add his own public key to authorized_keys.
The nano then signs this random value + the firmware version, using an embedded private key shared by some batches. O physically get the key from b. Write a first word including a first portion of.
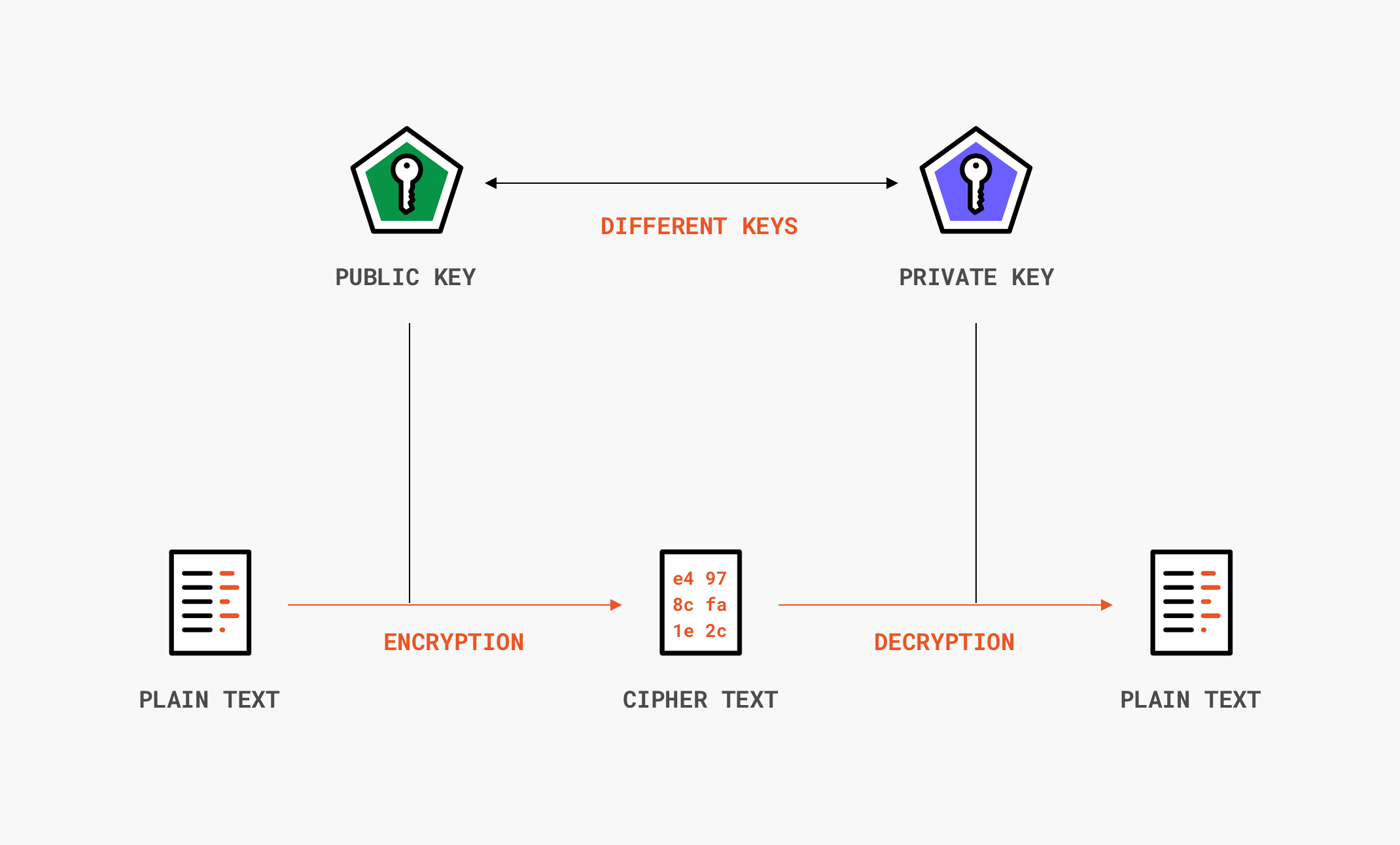
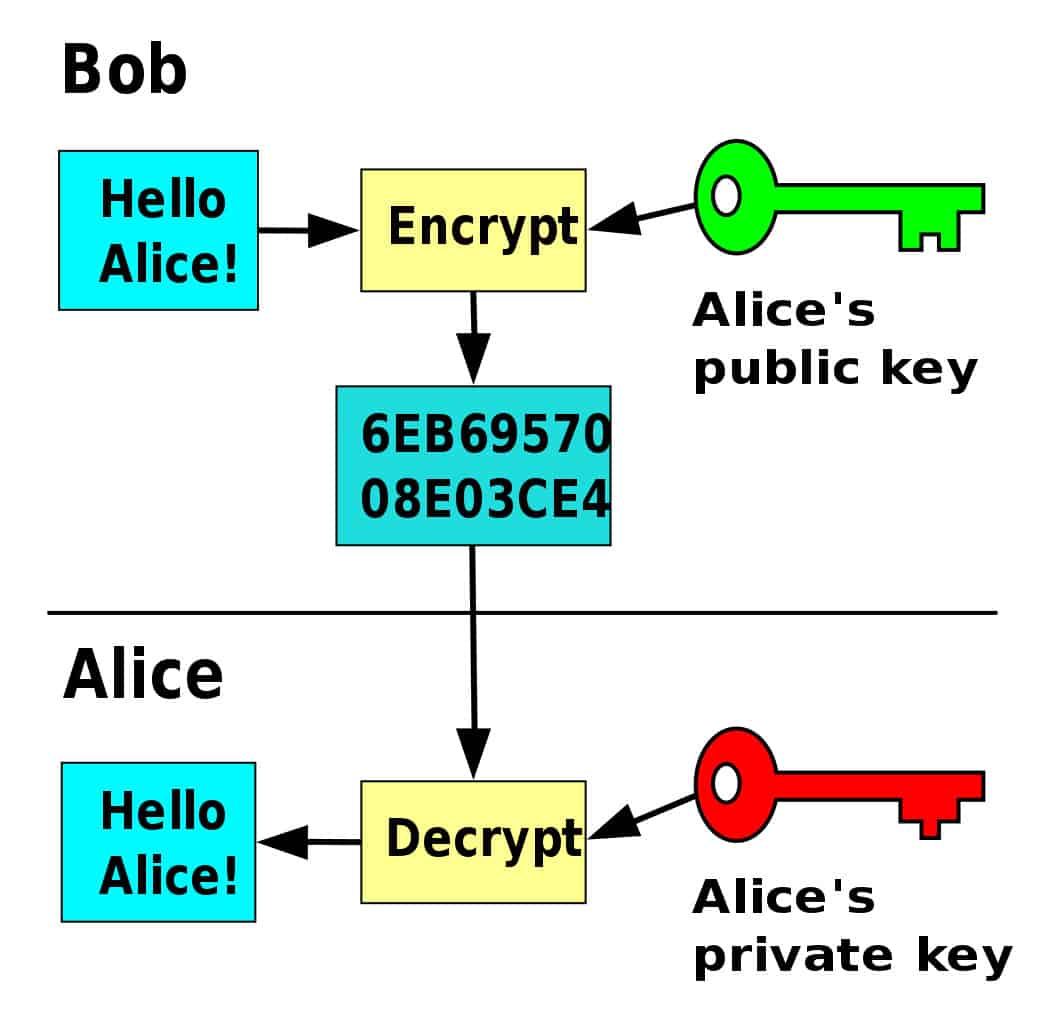
B could store her public key (pub) on a floppy disk and hand it to a. You could do this by making a detached. If you want to ensure that nobody can tamper with your data, we recommend the message authentication code (mac) primitive.
O verify a key by telephone. A computing device may include a cryptoprocessor that is configured to: Assume for instance that the application have a public key stored in the assembly to unpack an encrypted license key that validates the use of the application.
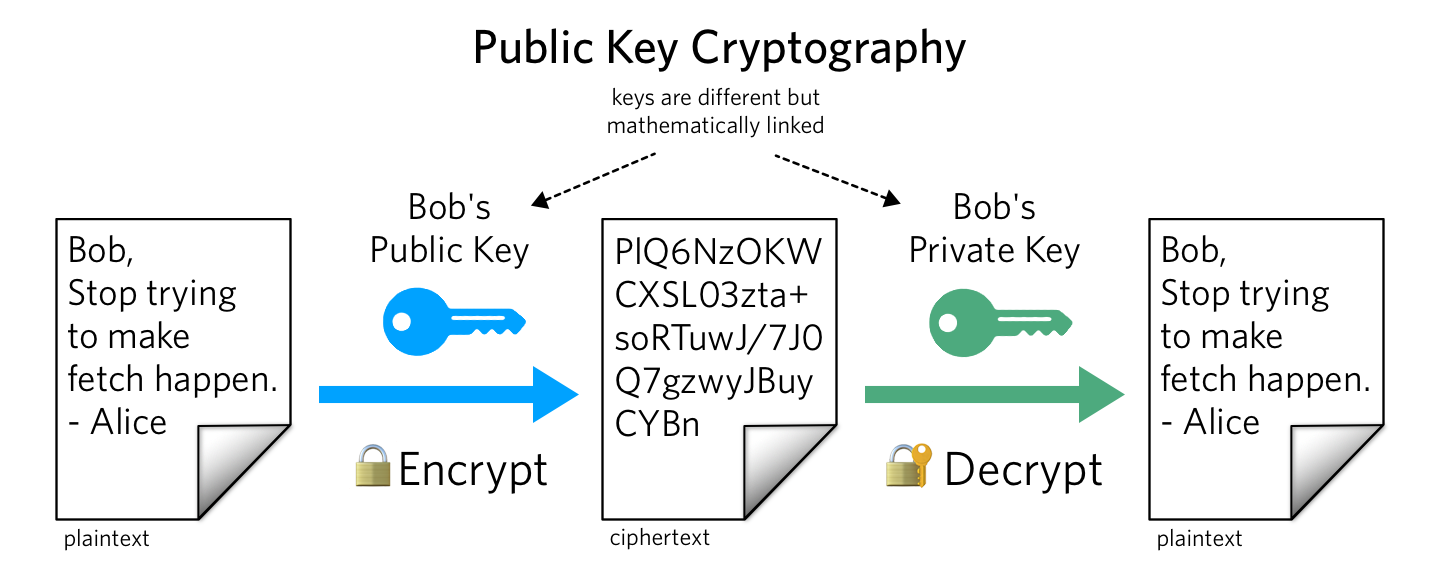
When you use someone's public key, make certain it has not been tampered with. A new public key from someone else should be trusted only if you got it directly from its. You could do this by making a detached.
For starters, one thing that i don't fully understand, is there. Here are 5 effective ways you can use for data tampering prevention: It uses a single key to generate message.
The reason for this question is that i'll like to investigate the means to protect sensitive data in an application. If a can recognize b on the phone, a could call b and ask. Disclosed is an apparatus and method to protect against key tampering.
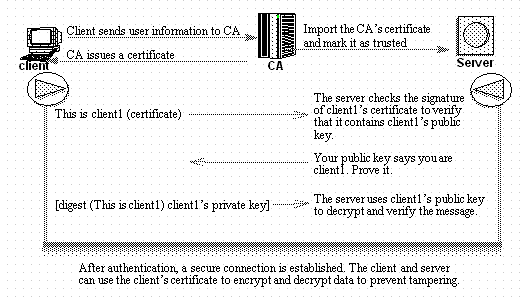
The chrome app knows the public key and. User’s guide v table of contents preface.